Seed and certificate storage
Overview
- To securely store the users' seeds used by LAM, we suggest you integrate HashiCorp Vault to benefit from authentication back-ends and encrypted-at-rest seeds.
- Hashicorp Vault is an open-source secret management tool specifically designed to control access to sensitive credentials, such as the seeds and certificates stored on LAM.
- By default, seeds are stored in a file readable by LAM. This means that the security of the authentication to the LAM depends on the network access policy and administration rights of the machine running LAM. Using HashiCorp Vault allows you to encrypt your seeds at rest, segregate their access, and enforce a layer of authentication to access them.
| Default file system | HashiCorp Vault | |
|---|---|---|
| Authentication method | Certificate and user seeds stored in clear on LAM | Certificate and user seeds encrypted on LAM |
| Login policy | No login policy implemented at the machine access level by default | Comprehensive login policies |
| Storage | Single Authorization Key for all API Operators | Different access token per API Operator |
- HashiCorp Vault also provides a framework to integrate with third-party authentication providers (such as OIDC) and allows defining complex access policies.
- For more information or additional support, refer to the Hashicorp Vault documentation.
Glossary
| Term | Definition |
|---|---|
| OIDC | Simple identity layer on top of the OAuth 2.0 protocol |
| userpass | Username and password |
Data flow
The following diagrams show how information flows between LAM and HashiCorp Vault.
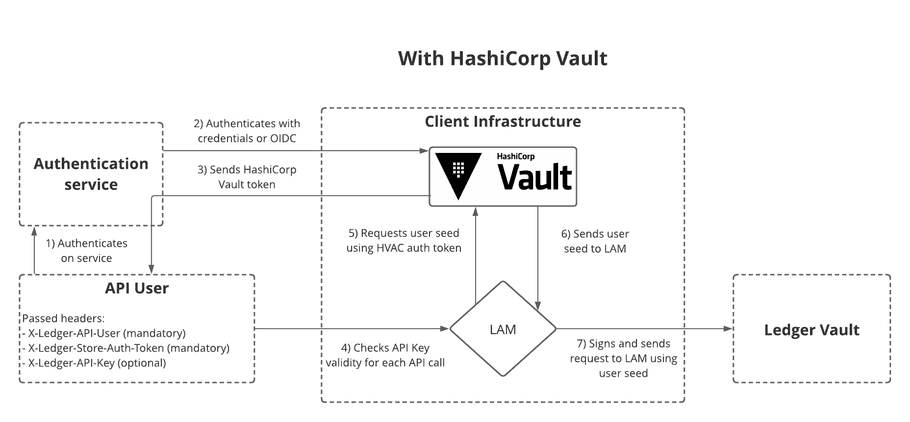

Before you begin
You must have:
- Onboarded your Ledger Vault workspace.
- Acquired sufficient knowledge on the functioning of HashiCorp Vault using their documentation .
- Configured HashiCorp Vault properly and run it on the client’s infrastructure.
- Read this article and ensured you adjust the scripts to fit production needs.
Instructions
Set up HashiCorp to authenticate with:
warning
Since a X-Ledger-API-User is mandatory, the first API User cannot be created via the HashiCorp Vault - only subsequent API users.